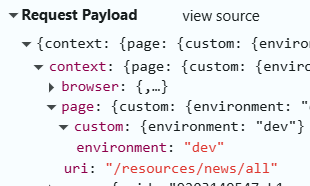
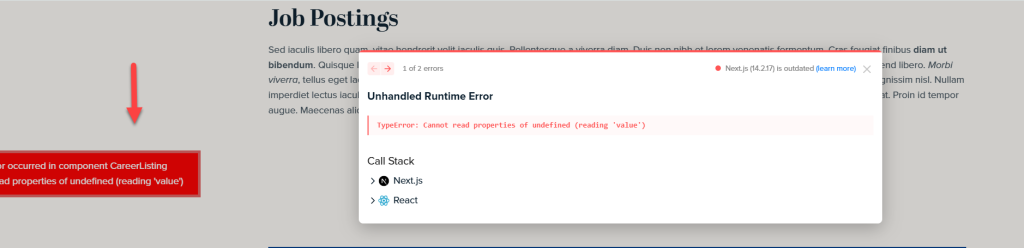
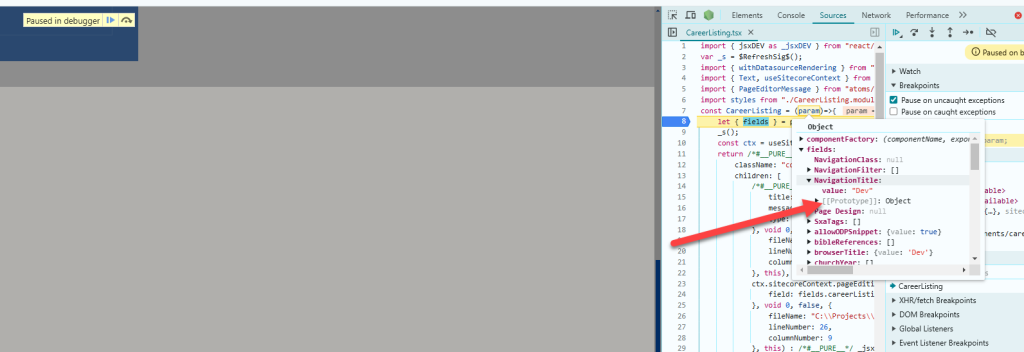
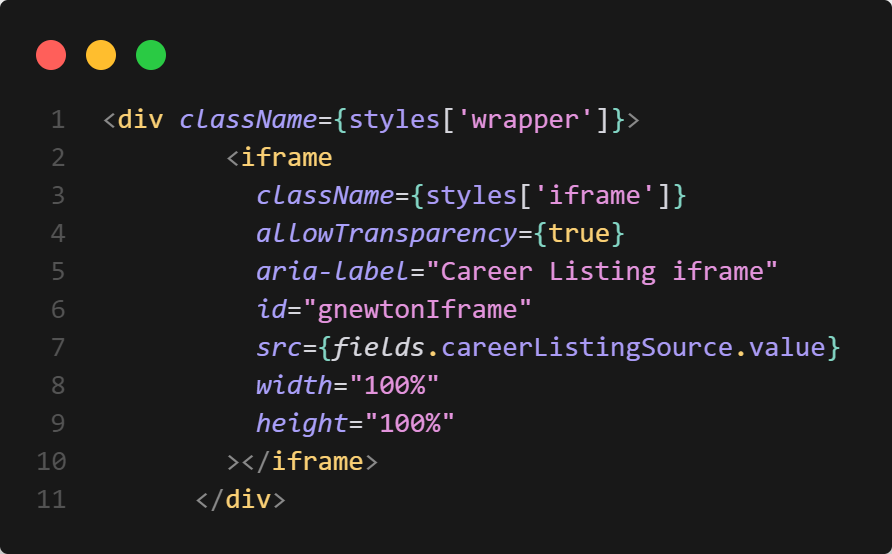
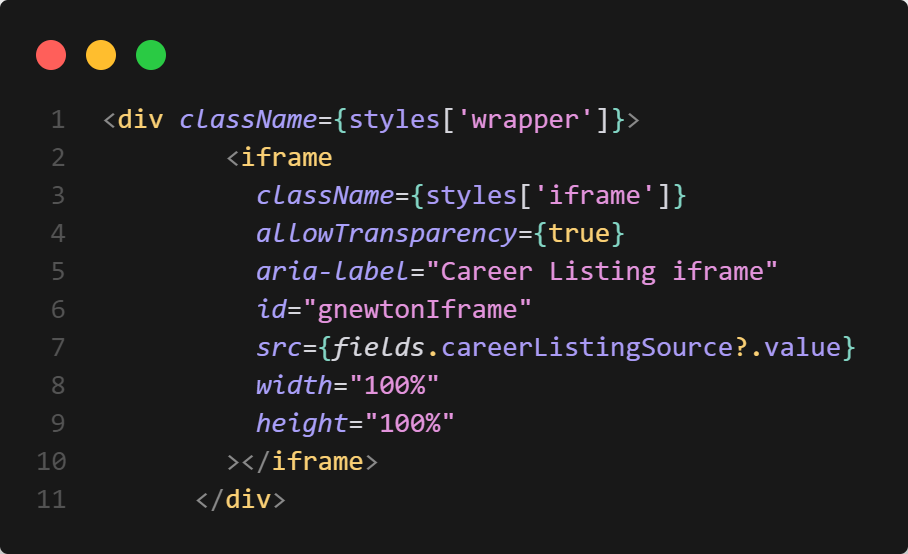
You might have noticed that when setting up URLs in Sitecore, the language is not always included in the URL—even if you’ve enabled languageEmbedding in the SXA Site settings.
Luckily, there’s a fix for this.
I followed the Next.js i18n routing guide, which recommends explicitly adding the “default” locale to your next.config.js. This is key to ensuring that language prefixes are consistently applied.
Here’s how your config should look:
// next.config.js
module.exports = {
i18n: {
locales: ['default', 'en', 'de', 'fr'], // Add 'default' intentionally
defaultLocale: 'en',
},
trailingSlash: true,
}
After updating your config, you’ll likely need to implement custom middleware to handle redirection when the locale is detected as default.
Here’s an example of a middleware plugin I implemented:
import { NextRequest, NextResponse } from 'next/server';
import { MiddlewarePlugin } from '..';
import config from 'temp/config';
const PUBLIC_FILE = /\.([^.]+)$/;
class MultilanguagePlugin implements MiddlewarePlugin {
// Ensure this plugin runs early in the middleware chain
order = 0.1;
async exec(req: NextRequest, res: NextResponse): Promise<NextResponse> {
if (
!(
req.nextUrl.pathname.startsWith('/_next') ||
req.nextUrl.pathname.includes('/api/') ||
req.nextUrl.pathname.includes('/robots.txt') ||
req.nextUrl.pathname.includes('/sitemap.xml') ||
req.nextUrl.pathname.includes('/sitemapindex.xml') ||
PUBLIC_FILE.test(req.nextUrl.pathname)
)
) {
if (req.nextUrl.locale === 'default') {
const locale = req.cookies.get('NEXT_LOCALE')?.value || config.defaultLanguage;
return NextResponse.redirect(
new URL(`/${locale}${req.nextUrl.pathname}${req.nextUrl.search}`, req.url),
301
);
}
}
return res;
}
}
export const multilanguagePlugin = new MultilanguagePlugin();
What this middleware does:
If the locale in the URL is default, it will look for a NEXT_LOCALE cookie or fall back to your configured default language. It then performs a 301 redirect to the correct language-prefixed path (e.g., /en/about instead of just /about).
This approach ensures that all visitors—regardless of whether they hit your site directly or via internal navigation—are consistently served URLs with the correct language code.
Patching the Link Resolver in Sitecore
To ensure that URLs generated within Sitecore always include the language code, I also patched the linkManager configuration by setting languageEmbedding="always".
<linkManager>
<providers>
<add name="myLinkProvider"
type="itecore.XA.Foundation.Multisite.LinkManager.LocalizableLinkProvider, Sitecore.XA.Foundation.Multisite"
cacheExpiration="5"
addAspxExtension="false"
alwaysIncludeServerUrl="false"
encodeNames="true"
languageEmbedding="always"
languageLocation="filePath"
lowercaseUrls="true"
shortenUrls="true"
useDisplayName="false" />
<add name="mySitemapLinkProvider"
type="itecore.XA.Foundation.Multisite.LinkManager.LocalizableLinkProvider, Sitecore.XA.Foundation.Multisite"
cacheExpiration="5"
addAspxExtension="false"
alwaysIncludeServerUrl="true"
encodeNames="true"
languageEmbedding="always"
languageLocation="filePath"
lowercaseUrls="true"
shortenUrls="true"
useDisplayName="false" />
</providers>
</linkManager>
By setting languageEmbedding="always", you enforce consistent language-prefixed URLs across all link generation in Sitecore, whether for internal navigation or sitemap XMLs.
Final Thoughts
Combining this Sitecore configuration with the Next.js i18n setup and middleware ensures that your multilingual site always respects language-specific routing—boosting SEO, improving UX, and keeping everything nice and consistent.